Valdenio Marinho A.K.A. "0xrh0d4m1n"
SOC Analyst

 Executive Summary
Executive Summary
I am passionate about cybersecurity, my fascination with hacking began in my youth and has remained a constant drive throughout my career. My journey started with an electrical engineering background, where I acquired a solid foundation in electronics and microcontrollers. Following in the footsteps of the most influential minds in IT and the trailblazing pioneers of the field, I left academia to carve out my own path, a decision fueled by a desire to apply the robust knowledge base I had acquired. This led me to web development.
Transitioning into web development, I rapidly evolved into a Full Stack Web Developer, a transformation made possible by the unwavering and invaluable support of great mentors around the world. My curiosity soon led me to the cutting-edge technology of blockchain and NFTs, where I was actively involved in innovative projects. However, it was the intricate and dynamic field of cybersecurity that truly captivated me, prompting a deep dive into cryptography, network security, and various security disciplines.
I have completed top-tier courses on leading cybersecurity platforms, staying ahead of industry trends and mastering the most current practices. My education has been greatly enhanced by hands-on experience in advanced labs, where I've tackled real-world scenarios to hone my skills. Additionally, I have extensively practiced advanced bug bounty hunting techniques, participating in numerous platforms worldwide.
Nowadays, I specialize in threat analysis, incident response, and mitigation strategies for large-scale cyber threats, particularly DDoS attacks and advanced network-based threats. As part of my role, I actively monitor, analyze, and counteract Layer 3, 4, and 7 attack vectors, ensuring business continuity and the security of mission-critical systems. I work with Web Application Firewalls (WAFs), SIEM, SOAR, and IDS/IPS solutions, optimizing detection and response mechanisms against sophisticated threats. My expertise extends to log analysis, monitoring, and network forensics, identifying attack patterns, distinguishing legitimate traffic from malicious activity, and reinforcing security perimeters.
Beyond defensive strategies, I have a strong focus on offensive security research, particularly threat modeling, threat hunting, and reverse engineering. To fully understand the evolving tactics of Advanced Persistent Threats (APTs), I engage in malware analysis and development, dissecting how advanced attack mechanisms operate. This allows me to anticipate adversary strategies, improve detection techniques, and craft better countermeasures against stealthy and persistent threats. My activities also involve deep forensic investigations, analyzing memory and disk artifacts, detecting rootkits, and leveraging sandboxing techniques to observe malware behavior in controlled environments during malware analysis experiments.
This comprehensive, hands-on experience has broadened my technical expertise and deepened my appreciation for the ever-evolving cybersecurity landscape. I stand with a solid understanding of defensive and offensive security operations, shaped by continuous practice and the humility gained from the Dunning-Kruger effect. I am committed to constant learning, always trying to stay ahead of adversaries, and pushing the boundaries of what’s possible in the digital world.
 Skills & Expertise
Skills & Expertise
Technical Skills
-
Penetration Testing

Simulating cyber attacks to identify and exploit security vulnerabilities.
-
Risk Assessment

Evaluating and prioritizing potential risks to minimize the impact.
-
Vulnerability Assessment

Systematically identifying and quantifying security vulnerabilities in systems.
-
Security Operations

Overseeing and maintaining a secure operational computing environment.
-
Incident Response

Effectively managing and mitigating cyber incidents to minimize damage and recovery time.
-
Cyber Threat Intel

Analyzing and interpreting information about potential cyber threats to prevent attacks.
Programming Languages
-
Nim

I'm still exploring new languages like Nim, trying to adeptly leverage Nim's efficiency and expressive syntax to craft secure, high-performance applications with a focus on cybersecurity tooling.
-
JavaScript

My JavaScript expertise come from a long time, my background as developer made me possible to perform penetration testing on web applications, identifying and exploiting client-side vulnerabilities.
-
Python

My Python skills are honed for scripting powerful cybersecurity tools and also automating complex security tasks.
-
Shell Script

I'm constantly using ShellScript for automating security processes and orchestrating system-level tasks on Unix/Linux platforms.
-
Rust

With my proficiency in Rust, I delve into low-level programming to create my own high-performance cybersecurity tools.
-
Assembly

My knowledge of Assembly allows me to perform meticulous analysis and reverse engineering of malware through tools like Ghidra.
Tools & Technologies
-
Burp Suite

Skilled in utilizing Burp Suite for comprehensive web application security testing and uncovering critical vulnerabilities.
-
OWASP Zed Attack Proxy

Proficient with OWASP ZAP for automated security scanning and targeted manual testing of web apps.
-
Greenbone OpenVAS

Experienced in deploying OpenVAS to scan and evaluate the security of network services and systems.
-
Tenable Nessus

Well-versed in using Nessus to identify a wide range of vulnerabilities and security issues within company infrastructure.
-
Qualys, Inc.

Adept at leveraging Qualys for vulnerability management and securing web applications and cloud environments.
-
Rapid7 Metasploit

Knowledgeable in applying Metasploit for developing and executing exploit code to assess network defenses.
-
Nmap

Capable of conducting advanced network discovery and security auditing with Nmap to reveal potential vulnerabilities.
-
Wireshark

Experienced in packet analysis with Wireshark, monitoring and diagnosing network traffic for security investigations.
-
Ghidra

Utilize Ghidra for reverse engineering, dissecting malicious code to understand and mitigate attack vectors.
 Certifications
Certifications
Fortinet
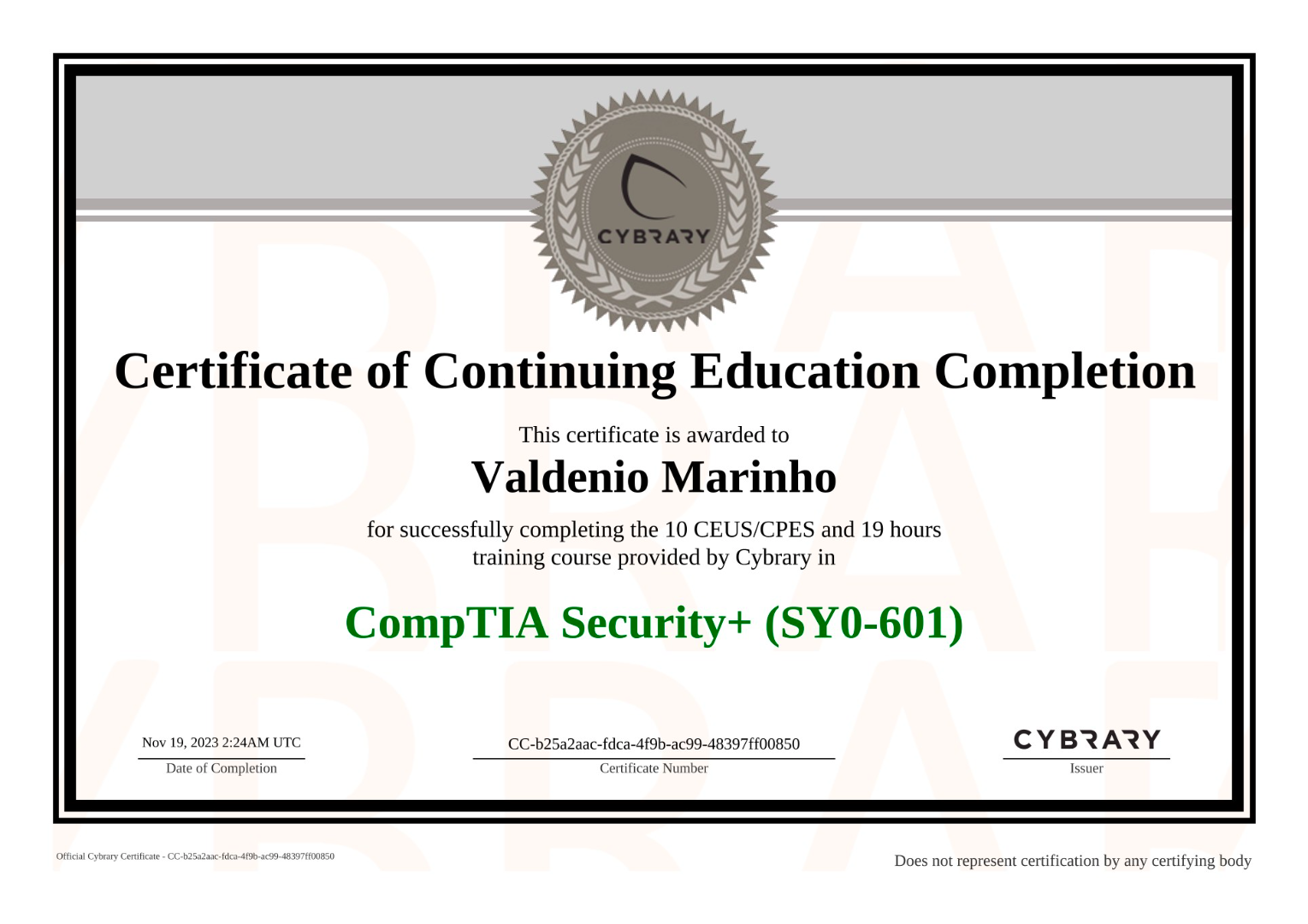
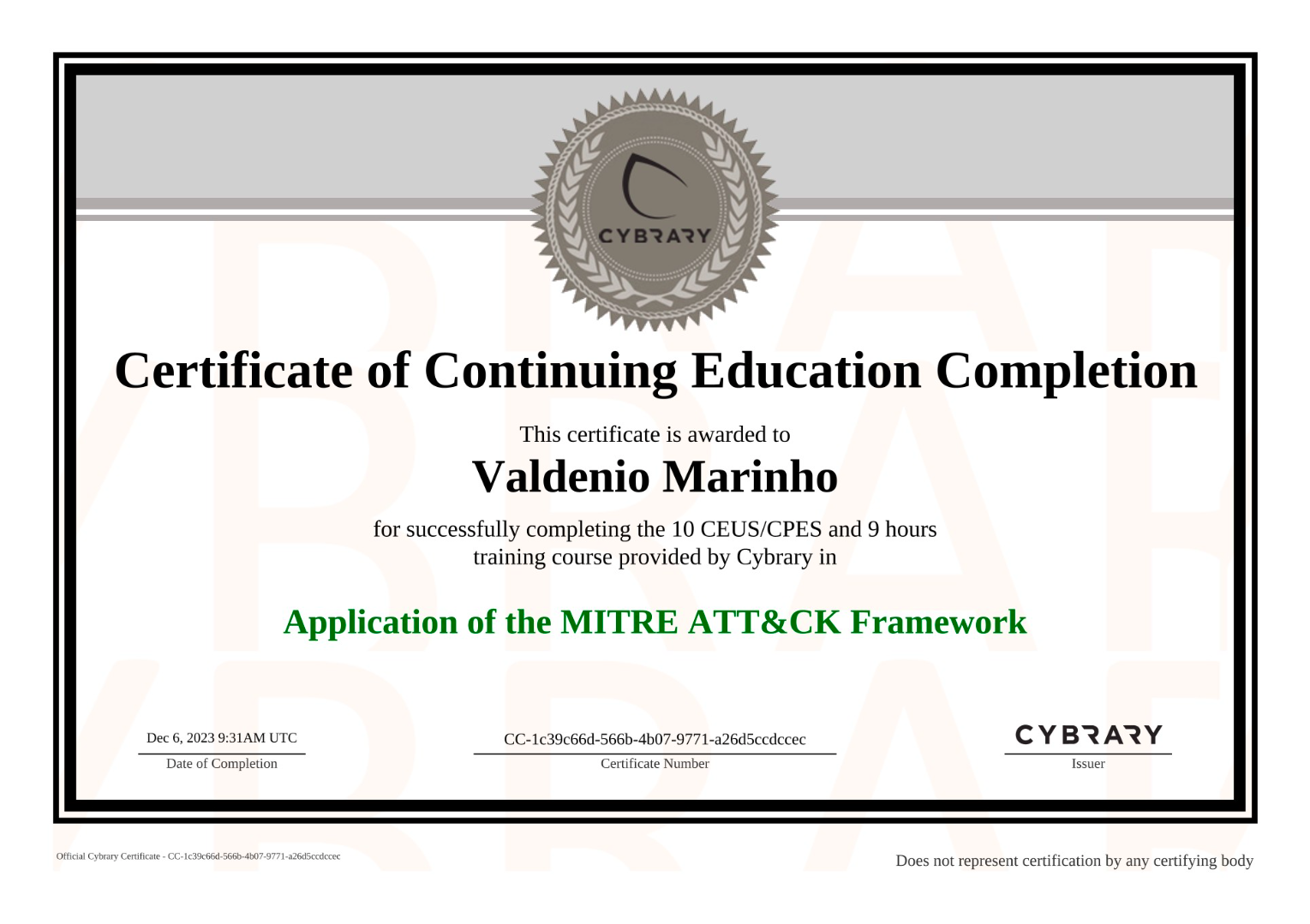
Cybrary
TCM Security
Other
 Professional Experience
Professional Experience
-
Nexusguard
SOC Analyst
Remote, Singapore
2024 — Present
- Monitor and analyze security events across enterprise systems using SIEM tools to detect, investigate, and respond to potential threats.
- Collaborate with incident response teams to mitigate risks and contain security incidents effectively.
- Conduct in-depth analysis of alerts to identify patterns indicative of cyber threats, enhancing detection and response capabilities.
- Generate detailed reports and presentations on threat intelligence findings, sharing actionable insights with stakeholders to fortify organizational security posture.
- Leverage Nexusguard's proprietary DDoS mitigation technologies to protect client infrastructures from volumetric, protocol-based, and application-layer attacks.
-
HackerOne, Bugcrowd, Intigriti
Cybersecurity Researcher
Remote, Worldwide
2023 — Present
- Successfully identified and reported a significant security vulnerability through HackerOne's Bug Bounty Program.
- Utilized advanced security testing platforms to perform comprehensive vulnerability assessments, identifying critical security flaws and weaknesses.
- Analyzed and reported findings from vulnerability discovery tools to provide actionable insights and recommendations for enhancing system security.
- Collaborated with cross-functional teams to address identified vulnerabilities, developing and implementing effective remediation strategies.
-
Freelancing
Fullstack Web Developer
Remote, Worldwide
2018 - 2022
- Designed and developed scalable, high-performance web applications using a range of technologies including HTML, CSS, JavaScript, and also frameworks.
- Managed software development lifecycle from initial planning and design to deployment and maintenance, ensuring project delivery on time and within budget.
- Integrated third-party APIs and services to enhance application functionality and user experience, while maintaining high standards of code quality and security.
- Conducted thorough testing and debugging to identify and resolve issues, ensuring optimal performance and reliability of web applications.
Education
-
B.Tech in Cybersecurity
University X
Snipped for privacy
2023 - 2025
-
Electrical Engineering
University Y
Snipped for privacy
2014 - 2016
 Projects
Projects
-
0xh3x73rs Team
Founding Member
2023 - 2024
- Co-founded a bug bounty team, demonstrating leadership and initiative in the cybersecurity field.
- Collaborated with team members to identify and report vulnerabilities in various web applications.
- Contributed to the successful identification of significant security flaws.
- Developed expertise in vulnerability research and reporting methodologies.
 Achievements
Achievements
 Languages
Languages
-
English:
Fluent -
Portuguese:
Fluent -
Spanish:
Conversational
 Download Resume
Download Resume
If you want to save my résumé, you can download it below, feel free to contact me any time!








































 Cyberdefenders
Cyberdefenders